The recent rise in cyber-attacks has raised substantial concerns among organizations who are considering migrating to the cloud and among ones that are already on it. But most importantly, these concerns are also raised by their end clients and potential clients. These end clients want to ensure that their service provider has implemented all the possible measures and best practices to protect their data and privacy while complying with all the relevant industry standards. In this article, we will examine what organizations are doing to protect their cloud deployments and how they can demonstrate to their clients that they have done everything possible to protect their data.
Cloud security is a “shared responsibility” between you and your cloud vendor
Today, all cloud service providers adhere to a “shared security responsibility” model, which means that although your organization’s security team maintains some responsibilities for security and the cloud provider takes on some responsibility as well. The line between the cloud provider’s responsibility and the organization’s responsibility varies between cloud service providers, but it is safe to say that typically the organization will be responsible for securing what’s under their direct control. This includes their data, code, resources’ configuration, etc. This means that although the cloud provider can be very secure, the organization’s deployment still depends on their ability to implement cloud security measures and best practices.
An experienced cloud security consultancy can assess your security posture and make it as secure as possible
Your organization’s IT department or even your existing security team may be very capable of securing your cloud deployment. But to verify that your deployment is indeed secured with the latest technologies and best practices, you should consider hiring a security consultancy. The external security consultancy can provide a new objective perspective and bring specialized cloud security expertise that has been accumulated and constantly updated by working with other clients with similar needs. And in any case, if you are required to demonstrate to clients that your cloud security posture is in top shape, you will need an outside objective security audit, which can be performed by cybersecurity consultancies.
How can a cloud security consultancy help you improve your cloud security posture?
In general, the process involves the following stages:
● Interviews to understand the company’s business, connection, and endpoints between components and environments, etc.
● An architecture review to check which best practices are met and which are not such as segmentation, edge protection, etc.
● Assessment which consists of a hands-on review of the cloud environment, network, and system components.
● Following the assessment and architectural review, an assessment report is generated, which maps the risks, security gaps, vulnerabilities, and recommendations.
● This report is then used to remediate the findings and improve the security posture.
● Finally, to check that the gaps were successfully remediated, a penetration test is conducted, followed by a final report.
Architecture review and assessment
This is the most comprehensive phase, as it includes the comprehensive assessment across the entire deployment, offering high coverage. As part of this process the following areas are examined:
· Asses the specific cloud security risks relating to your data profile and company’s business – security risks may vary based on your deployment’s characteristics. For example, if your deployment includes regulated or sensitive information, the security measures should conform to the relevant regulation and specific best practices should be applied to protect this data.
· Examine how sensitive data is accessed and shared – If your cloud deployment includes sensitive information, such as Personal Identifiable Information (PII), the cloud security consultancy will examine how this sensitive data is accessed and shared. This includes checking the permissions on your cloud files and folders, access context like user roles, location, etc.
· Mapping of the connections and third parties – all the connections to the environment are mapped, including IP addresses that are exposed externally, domains, APIs, all third-party connections (remote access, SSH, etc.), VPN connection, and more.
· Discovering “hidden” cloud resources – in many cases security vulnerabilities are found in “dormant resources” that are not in use regularly. These resources are usually not protected and patched and can therefore pose a serious risk. The cloud security consultancy will examine the SIEM logs to find these “unknown” cloud services and then assess the risks associated with them.
· Examine the existing configurations – the cloud security consultancy will examine the IaaS environment configuration and look for vulnerabilities based on misconfigured settings, such as identity and access management, network configuration, and encryption configurations.
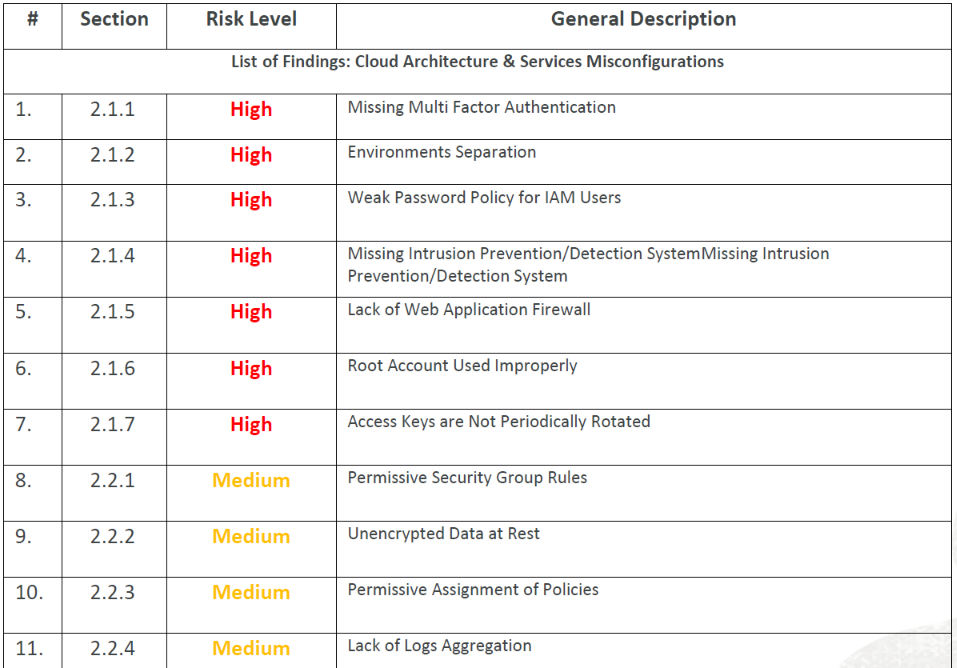
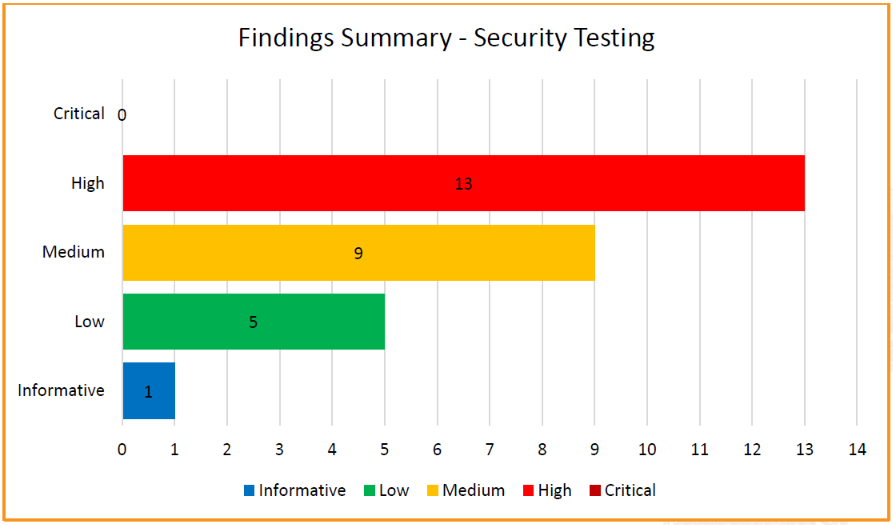
Producing an Assessment Report based on the findings
Following the security assessment/audit, a detailed report is created, mapping all the gaps and vulnerabilities that were found in your deployment, while prioritizing them by their overall risk. The report evaluates the Cloud Security posture based on industry best practices as well as the cloud security consultancy’s experience. This report forms the basis for an action plan to improve the security posture of your cloud deployment.
Fixing the security gaps
Based on the report, different measures are taken to remediate the security gaps. Whether you do it yourself or through the cloud constancy, there are many measures that can be taken to improve the cloud security posture. For example, increase verification requirements for high-risk access scenarios, including the implementation of two-factor authentication; ensuring that Cloud identity & access policies are based on least privilege; ensuring that Edge protection is implemented correctly, and more.
Performing penetration testing to verify that the security issues were remediated
At this stage, you want to ensure that the measures taken to improve your security posture have actually helped, by performing a penetration test. A penetration test is a controlled attempt to breach into an organization or a system to verify the damage that can be caused to a business by real attackers. Penetration testers use the same tools, techniques, and processes as the attackers. This practice allows decision-makers to prioritize resources allocation to strengthen cyber resilience of the business. Cloud penetration test can be performed internally (inside the perimeter) or externally (outside the perimeter). The penetration test can be performed using a black, grey, or white box security assessment approach. One of the benefits of the penetration test is that it tests the security of the application level as well as underlying cloud infrastructure/environment.
Following the penetration test, a penetration test report is issued, which shows whether any vulnerabilities and misconfiguration could have been exploited. This report or an attestation letter from the consultancy can be shown to concerned clients as a proof that you are secure.
Conclusion
As we’ve seen, although cloud security can be handled by a combination of your organization’s IT/security team and the measures provided by the cloud service provider, in most cases there is always room to improve the security posture. After all, security is an “all or nothing” game, which means that even if you properly secure most of your cloud deployment, hackers will usually find vulnerabilities that are “under your radar”. For this reason, it is extremely important to find an experienced cloud security consultancy that can provide an outside/objective perspective and help you demonstrate you are secure for yourself and for your clients.
Related Blog posts:







