I don’t think you ever hear the phrase “we are cutting back on our security budget”, right? A security budget never shrinks, it always grows. But security experts will tell you that getting all the security money can buy is usually not necessary. Instead, you need to map out the threats that may be relevant to your organization and only then match these threats with the appropriate security measures.
To put it in an exaggerated manner, one should not secure an office supplies online store in the same manner as a bank. It’s not that the store owner should care less about being attacked, it’s that the more sophisticated attackers would not be interested in the store as much as they would be interested in the bank, and therefore the store owner should match the sophistication of the security measures to the expected threat level.
It’s the same as securing a physical facility, you would probably not put up huge fences, patrol guards, cameras, and a swat team on standby if you live in a safe neighborhood and you don’t have anything that would interest the burglars. In this blog post I will try to roughly map out the types of threats and the security levels that would probably be appropriate to them.
Types of attackers
To understand the various types of threats we need to first classify the attackers and understand what drives them and their sophistication level.
- Script kiddie – A script kiddie, skiddie, or skid is an unskilled individual who uses scripts or programs, developed by others to attack computer systems and networks and deface websites. Their motivation varies, it could be part of a prank, curiosity, to an attempt to impress their friends or gain credit in computer-enthusiast communities. This type of attackers constitute the vast majority of attackers and it is estimated at around 80%.
- Hacker/cracker – a hacker is a computer expert who utilizes their technical knowledge of bugs or exploits to break into computer systems and access data. Unlike the script kiddies, hackers perform their own research and use their own knowledge of vulnerabilities in systems. These attackers constitute around 15%-20% of attackers.
- Elite – the most skilled type of attackers, Elite attackers will usually discover zero-day vulnerabilities and develop zero-day exploits. It is incredibly difficult to defend against these attackers. But luckily they constitute only 1%-3% of attackers.
These various attackers usually operate as part of a group. There are four types of groups:
- Unstructured – these are usually groups that are spontaneously organized, usually through social networks, for example, a group of political activists. They have very limited resources and often no resources at all. Their knowledge or skill level is very limited, as they are usually script kiddies, which in some cases are joined by hackers. They usually attack random opportunities that come their way, not targeted attacks. This means that they browse through a multitude of targets to find one that has vulnerabilities that can be easily exploited.
- Structured – these are groups that are organized with a specific purpose. For example, to steal or expose certain information from a specific target. They have resources that can last for months and are used for the development of attack tools, botnet networks, and more. In this case the individual participating in the attacks are hackers.
- Highly structured – these groups are similar to the structured groups but they usually have more resources that can last for years. They are usually financed or run by a criminal organization. They have the knowledge and abilities to develop crimeware. They are therefore capable of bypassing sophisticated security measures, including the ones used by large organizations, such as banks. The highly structured groups employ hackers and in some cases may also have elite attackers.
- Nation state – this is a highly structured group that is operated by states. These are usually intelligence organizations that deal with cyber warfare. They usually target other states and have vast amounts of resources. They usually use APT (Advanced Persistent Threat) attacks that are very difficult to detect. Nation state groups employ highly trained elite attackers and hackers.
How these categories apply to security
The combination of mapping the assets of your organization and understanding the intent of the various groups, their sophistication level, and the resources they have at their disposal, can help assess the threats that could be relevant to your business. For example, strategic state resources should be protected against nation state groups. This means that they should expect sophisticated and unpredictable zero day attacks, APTs, etc. In many cases their most sensitive information is managed in offline or air gapped locations and they use several layers of protection.
A bank can assume that they can be targeted by highly structured groups, which are run by well-funded criminal organizations and include elite hackers that use zero-day exploits.
On the other hand, a small online store would not interest the nation state and highly structured groups. In most cases they could be attacked by unstructured groups of script kiddies with very limited resources, who will pursue the attack only if they find vulnerabilities that really “stand out” and are easy to exploit.
So for the small e-commerce groups, as long as they comply with the security best practices of their industry and according to their size, they will probably not attract the unstructured groups, who will prefer to move on to another online retailer that may be easier to hack.
Security is more than just security systems
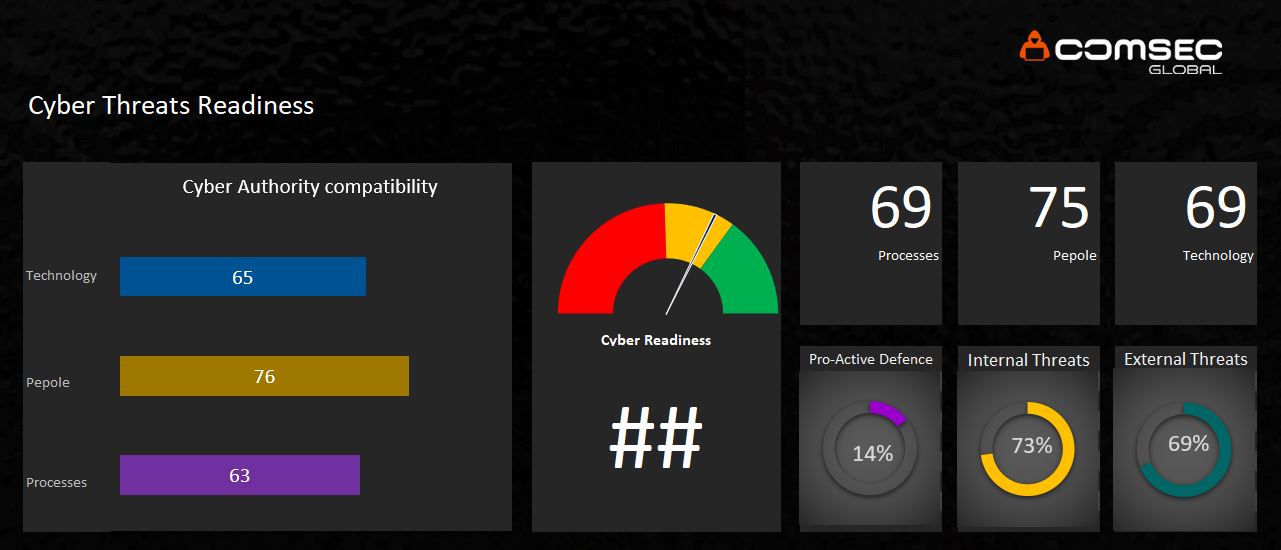
But security is more than just security technology that you can buy. It is actually the combination of people, processes, and technology that matters. Each of these elements is dependent on the other. For example, you may have state-of-the-art security technology, yet if an employee exposes their login credentials, the security technology becomes useless. In most organization the weakest link is the human factor. And for this reason, as part of our Organization Cyber Readiness Assessment , we check issues concerning the security technology in place, but also issues concerning employee/personnel security training and the procedures that are put in place to ensure the organization is also protected from non-technology attack such as social engineering attacks.
Adjusting the security posture scoring to the business profile and threat levels
We conduct the Organization Cyber Readiness Assessment through a simple tool that we built, which is also adjusted to match the business profile and the related threat levels. The tool generates a security dashboard that provides situational awareness of the organization’s security posture on all layers (i.e. technology, people, and processes). However, the score of the readiness level is adjusted to the specific industry and organization size.
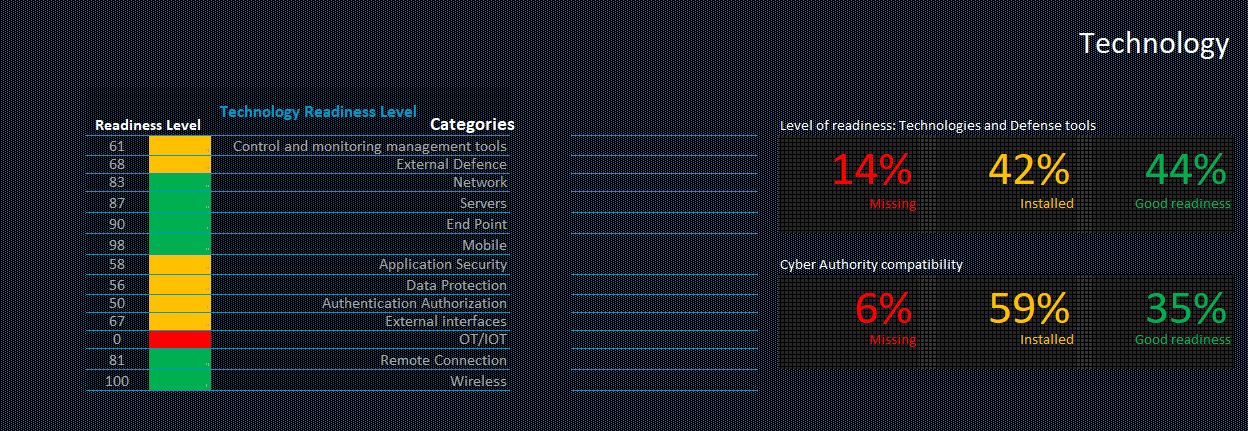
As we’ve seen, security is not a one size fits all product. Every organization is different and the threats can be related to different characteristics such as size, industry, its assets, the sensitivity level of the organization’s data, and much more. Understanding the threats and the intent and abilities of the various types of attackers can help optimize the required security levels so you don’t end up spending too much on your security.







