
Red Team tactics – breaching the lines of defense
The most challenging element of a Red Team engagement is often breaching the external perimeter of the organization and attaining domain credentials. Companies invest a

The most challenging element of a Red Team engagement is often breaching the external perimeter of the organization and attaining domain credentials. Companies invest a

The one vulnerability for which there can never be a patch, update or new anti-virus is that which is human. We can install the latest

In August 2019, a very secure and sensitive organization commissioned the Comsec Red Team to carry out a Social Engineering (SE) project. The customer requested

Containers, Orchestration, Docker, Kubernetes; We hear about this technology more and more every day. Use of containers and containerization became a natural choice by modern

The new OWASP IoT Top 10[1] released on December 25th 2018 is an attempt to unify several problems that multiple parts of an organization face

Come and meet Josh Grossman, one of our Application Division team leaders, at AppSec USA 2018 being held in San Jose, California in October!
Tiennot van Dilst- Principal Consultant / Delivery Manager – Comsec Benelux During my career as a CSO and Security Consultant, I have worked with the
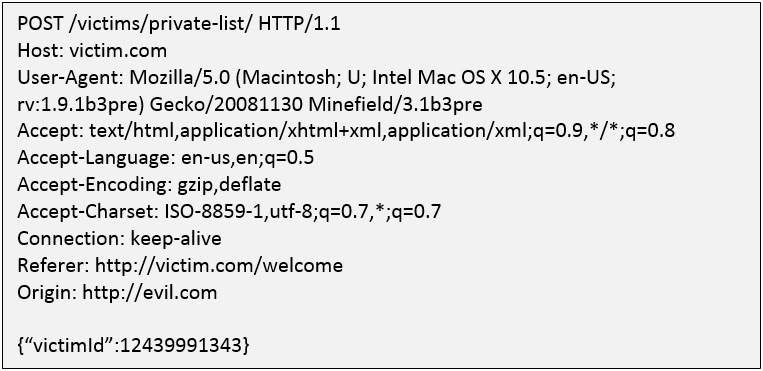
During our daily routine, we face lots of different kinds of web applications, which are built differently from one another. Sometimes the developers have the
Hello everyoneAfter a short break, ComTech is back. Today’s post will talk about something that is relevant to every pentest, the do’s and the don’ts
HelloFollowing my #defcon25 lecture in Las vegas, “Call the plumber – you have a leak in your (named) pipe” (https://www.defcon.org/html/defcon-25/dc-25-speakers.html#GCohen), here is the presentation file:https://drive.google.com/open?id=0B3_AmubjewYTVERidTVGZW5uRnM
