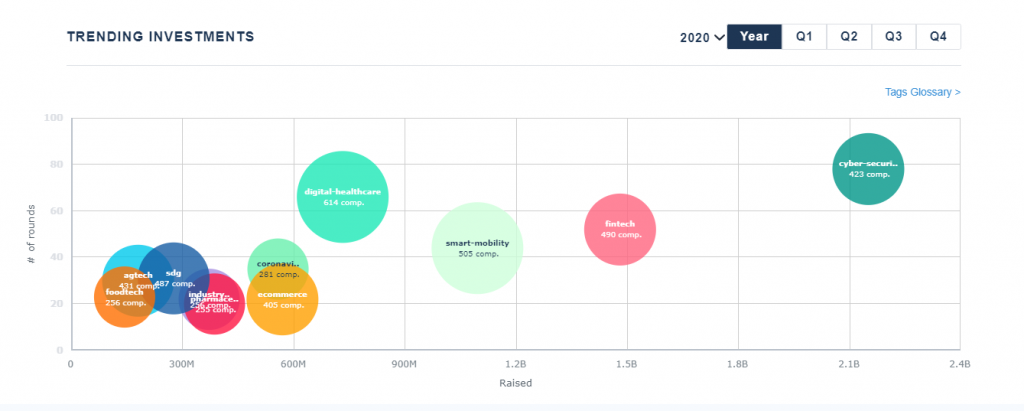
Israel is attracting attention in various advanced technology fields such as smart mobility, health tech, and fintech, but cyber security is by far the strongest. Looking at the Start-up Nation Central site, it is clear that companies in the cybersecurity sector will continue to raise huge sums of $ 2.2B in 2020, which sets them apart from other sectors.
There are various factors behind the secret of its strength, one of which is the existence of the field of Offensive Security . In server security, offense and defense are two sides of the same coin, and Israel can develop excellent defense technology only because it knows the know-how of offense. In that sense, it is no exaggeration to say that it is difficult to create excellent cyber defense technology in Japan, which does not have offense capabilities (in principle, exclusive defense). If you look at Comsec Global ‘s proven service in the Offensive Security field, you can see what it means to be “attack and defense are two sides of the same coin.”
Providing tailor-made solutions
Comsec Global is not a startup, but a mid-sized company with 32 years of experience, providing cybersecurity consulting services rather than individual products. Most of the 160 employees are engineers, and it is a major feature that we have specialists with experience in cyber intelligence at IDF (Israel Defense Force). It is well known that many Israeli companies have very good technologies and products, but most of them are stand-alone products. When Japanese companies use it, it is necessary to tailor it to a solution that is well combined with the existing system. Companies that do not have enough engineers often rely on SI (system integrator) companies to design, build, and operate in-house systems, and tend to seek network and security as an integrated solution. is. Comsec Global does not make many in-house products, but it is expressed as “consulting” because it provides a service that finds the best product for the customer and builds it in the existing system, so to speak, a “tailor-made solution”. I will.
Its service range is wide, but it is particularly strong in Offensive Security, so I will introduce the outline. The service that Comsec provides as Offensive Security is
① Threat intelligence service
② DDoS simulation D.Storm
③ Table top simulation
④ Ransomware exercise
⑤ Red team exercise
⑥ Incident Response Team Support
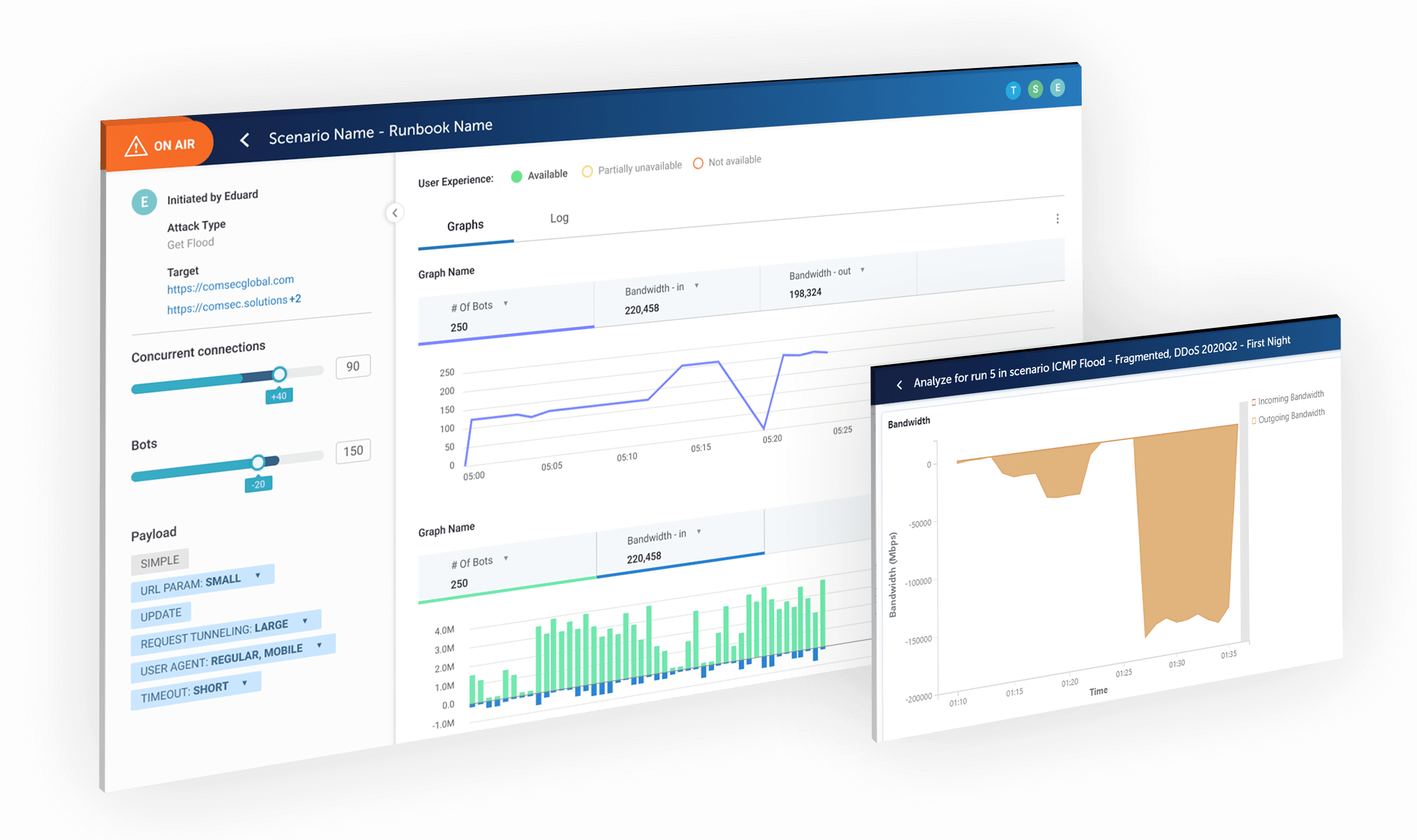
D.Storm Service
① Threat intelligence service
This service collects and analyzes information about customers from open WEB such as SNS, dark WEB where attackers are active, and deep WEB, and gives reports and real-time alerts. Like the famous Unit 8200, the IDF has outstanding threat intelligence research and analysis capabilities. Engineers with that experience and know-how can find signs of an actual attack before it occurs, so appropriate measures can be taken. This analysis know-how is not something that you can acquire overnight.
② DDoS simulation D.Storm
In a nutshell, DDoS attacks come in many variations, including Volumetric Attacks, Application attacks, HTTP / S floods, TCP & UDP floods, Infrastructure attacks, and Login floods. Comsec possesses all types of attack know-how and can freely create combinations of them. Although it is expressed as a simulation, it is actually an actual attack managed so that it can be stopped immediately. By conducting this simulation on a regular basis and finding out your weaknesses, you will be able to evolve into an attack-resistant system.
③ Table top simulation
Rather than a security expert, it is a training that involves members of various departments of the organization, including management. Security measures are desk training that recognizes that it is not something that is left to specialists alone, but that it is handled by a team, and that each person learns what to do in the event of an incident under the guidance of a specialist. .. Again, the fact that the instructor has attack know-how is reflected in the content of the instruction.
④ Ransomware exercise
In order to deal with the increasing number of ransomware in recent years, we first visualize the systems and assets of the organization and understand what kind of attacks are possible from the attacker’s point of view. Then, through actual attack simulation exercises, we will provide recovery plans, examination and advice on more resistant organizations and systems, what to do in the unlikely event of an attack.
⑤ Red team exercise
This is an exercise to experience the “real attack” that is most lacking in Japan. Engineers who have actually experienced “attacks on others” are extremely rare in Japan, and even if they understand vulnerabilities and attack methods as “technical knowledge”, there is a gap between them and actual attacks. Exists. In addition, most existing exercise services experience attacks of fixed scenarios and train countermeasures on platforms with inherent vulnerabilities prepared in advance, but Comsec exercises analyze the customer’s environment. Find vulnerabilities and let relevant threats experience attacks that affect your business. Of course, we also provide consulting on countermeasures.
⑥ Incident Response Team Support
Even if you have an incident response team of good engineers, it’s a never-ending battle with attackers who are constantly developing new methods. It is a service that supports this team from the standpoint of an expert with attack know-how.
Looking at these item names alone, it may seem that Japanese cybersecurity companies are also offering similar services. However, when you actually see the know-how of someone who has worked in IDF intelligence for several years, you will be surprised at the difference. Recently, there have been many cyber incidents that are thought to be caused by the spread of remote work, such as the leakage of internal information from game companies. I think it is necessary to reaffirm the fact that accurate defense is possible because of the power to attack.







